7 Red Flags to Alert You to a Potential Phishing Scam
Wednesday, October 12, 2022
October is Cybersecurity Awareness Month, the digital world is full of phishing scams and the more time you spend online, the more you encounter. Scammers have many ways to hook you. Some of the most popular scams involve requests for gift cards, employment offers, and account deactivation threats. Use these red flags to spot phishing scams:
A DEMAND FOR URGENT ACTION:
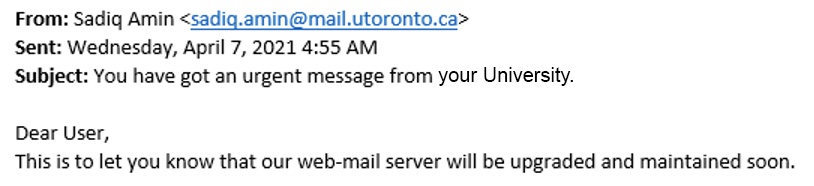
Be suspicious of any email that asks you to take action, click a link, or divulge information immediately to claim a reward or avoid penalty. This is common technique phishing emails use to create a false sense of urgency, so recipients have less time to evaluate the validity of the message.
SPELLING AND GRAMMAE MISTAKES:
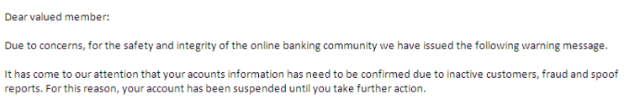
Many phishing emails contain very obvious spelling and grammar mistakes such as “acounts” and the phrase “has need” in this example. Some of these mistakes are actually included on purpose to weed out the people who are observant enough to recognize them and question the legitimacy of the email.
GENERIC GREETINGS OR SALUTATIONS:
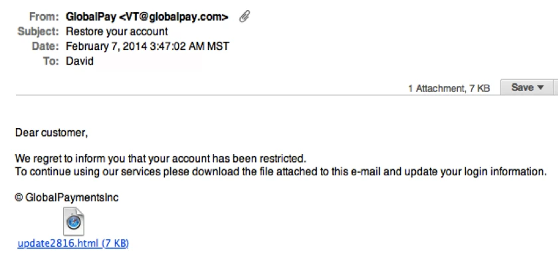
Phishing emails often contain very generic greetings or even no greeting at all. Common generic greetings include “dear customer,” “dear account holder,” “dear user,” “dear sir/madam,” or “dear valued member.” If an email from an apparent trusted source does not address you directly by name, that could be a red flag.
INCONSISTENT LINKS, EMAIL ADDRESSES, OR DOMAIN NAMES:
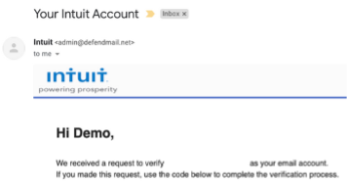
Another obvious sign that an email may be illegitimate is if the email address of the sender does not match the purported affiliated company. Also, if the email includes a link with a website domain name that does not match the content of the message, that is another red flag that the link will not lead to what they claim it will.
SUSPICIOUS ATTACHMENTS:
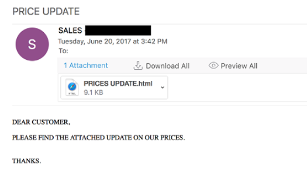
A common request in phishing emails is asking the recipient to click a link or open an attachment. A more obvious sign that an attachment may be malicious is if it is an “.exe” or executable file, which are dangerous because clicking them can execute a program on your computer. A newer and more sneaky attachment type in phishing emails is a “.html” attachment that leads the recipient to an HTML page. These pages often request entry of usernames and passwords, and they send that information to the scammer.
AN OFFER THAT'S 'TOO GOOD TO BE TRUE':
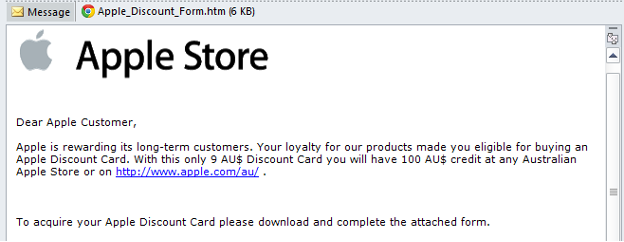
One of the more apparent red flags in a phishing emails is simply an offer that is too good to be true. Many scams will tell you that you have won a contest, have a bonus to claim, or are eligible for a giftcard. Be critical of any message that claims you have been offered money or a ridiculous discount, especially if you have to pay a small amount to receive it.
REQUESTS FOR PERSONAL INFORMATION:
Such as login credentials, financial information, SSN's, or other sensitive data.
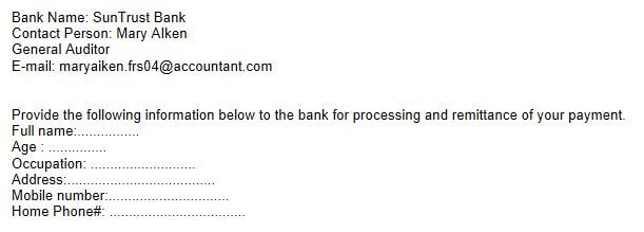
Requests over email for personal information, financial information, or other sensitive data is another easy way to identify a phishing scam. Never disclose information related to your identity such as your SSN over email. If you feel like verifying the legitimacy of the message, contact the institution that the message claims to have been sent from and ask if they really need that information from you.
An email that includes one or more of these red flags is likely to be a phish.
When you receive a phishing email, send it to abuse@uga.edu for review.

